Virtual Private Cloud is a full data center within the AWS cloud. Amazon now makes it possible for you to rent a piece of the AWS infrastructure to build and manage your own ecosystem. You have full control of your servers, storage and networking.
Within this ecosystem, you can create a series of public and private subnets and within there, a collection of EC2 instances for web servers, database servers, devops, etc.
For example, suppose you want to create a Wordpress blog but you want your MySQL database to live on a private server. By creating a private subnet, you can install an AWS Relational Database (RDS) that is separate from your public Wordpress server. The benefit from this structure is that it's slightly more defensible from a DDoS attack, hopefully. ;-).
Anatomy of a VPC

At its very core, Virtual Private Cloud's consist of:
- Subnets
- Public
- Private
- Firewalls
- Security Groups
- Network Access Control Lists (ACL)
- Internet gateways
- Route tables
When you create a new VPC, by default you will get a:
- Route Table
- Firewall
- Security Group
- Access Control List
You will not get a default subnet or a route table.
Managing Subnets

Before we can structure our subnets, we first need to understand how we use addresses to help organize.
Address Classes
There are many types of addresses classes used use to organize a VPC. They are referred to as Class A, Class B, Class C, etc.
Class A
1.0.0.1 to 126.255.255.254
If you've ever printed from an office, you may have seen something like this:
10.x.x.x
Class B
128.1.0.1 to 191.255.255.254
Class C
192.0.1.1 to 223.255.254.254
If you've ever shared a file on a Mac, this might look familiar to you.
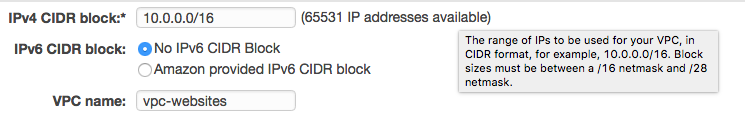
CIDR Block
When creating a new VPC, the first step is to usually take what AWS provides and partition it. Partitioning your VPC makes it easier to defend, control, manage and optimize.
The first step to partitioning a VPC is assigning an IP CIDR block. A CIDR block is a top-level, pool of addresses that your network will use and take a slice from.
From within this CIDR block, you will then partition your addresses by creating subnets.
The most common CIDR block is 10.0.0.0/16 and AWS will often provide it as a default.
Subnet Types
Subnets are used to partition your VPC and the most common thing to do is create both a public and private subnet.
Here is a diagram:
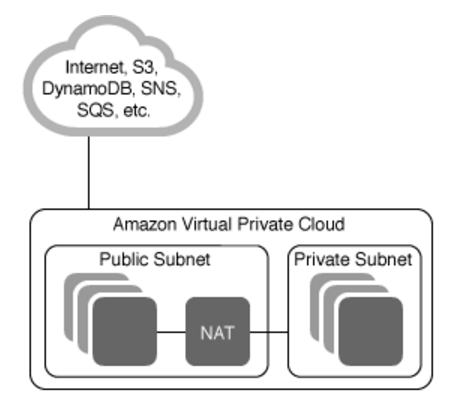
- A Public Subnet will have direct access to the Internet. This is done through an Internet Gateway.
- A Private Subnet can access the Internet through a NAT or quarantined so that it doesn't connect to the public at all.
Subnet IP Adresses
Subnets use IP addresses to assign devices to your network.
There are three different types of private IP address ranges and some of these might look familiar:
10.0.0.0 - 10.255.255.255 (10/8 prefix)
172.16.0.0 - 172.31.255.255 (172.16/12 prefix)
192.168.0.0 - 192.168.255.255 (192.168/16 prefix)
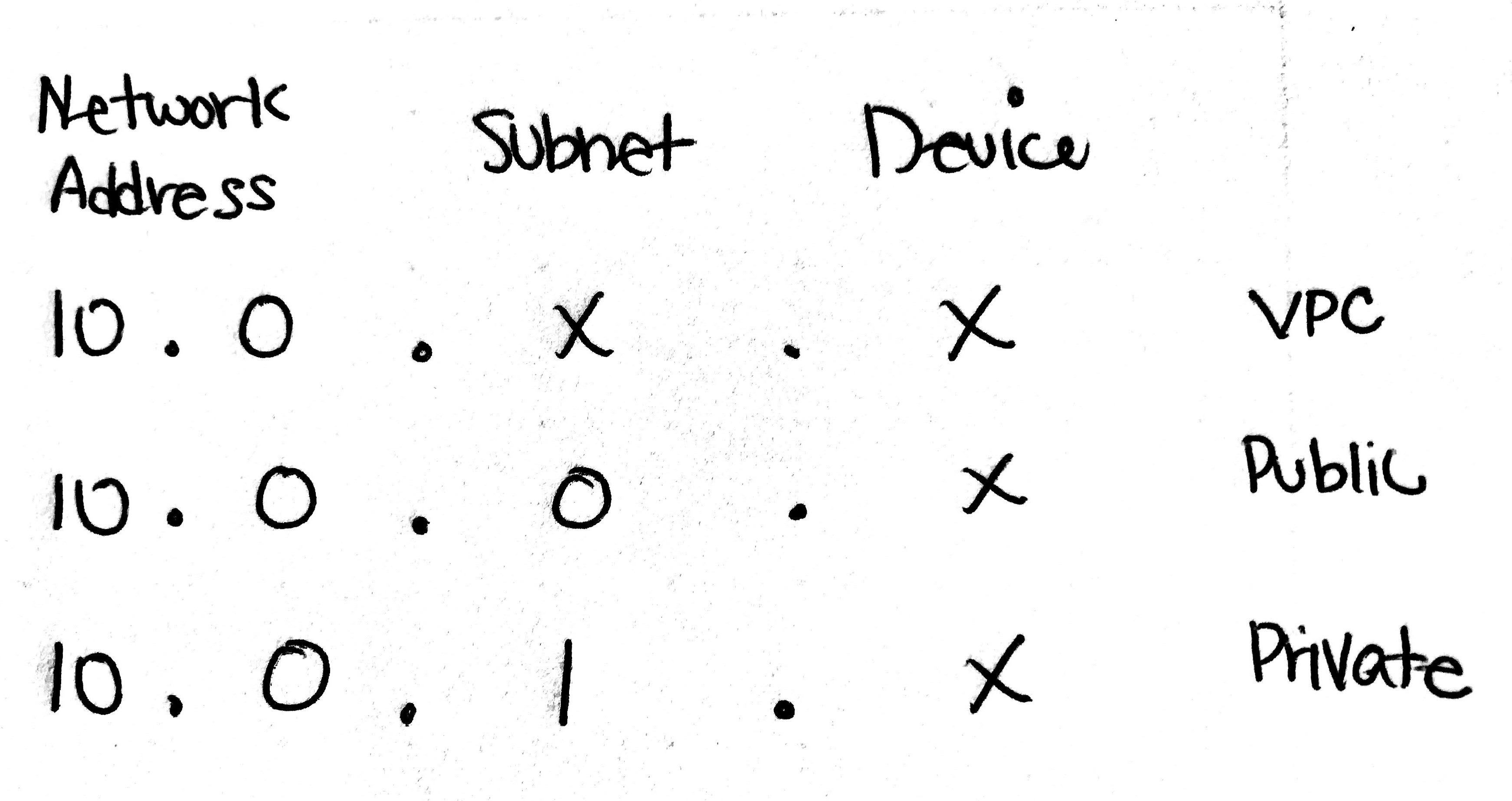
To briefly explain what this means, IPv4 addresses are broken into 4 sets of 8 bits (octets) like this:
10.0.0.0/16
Each octet represents 8 bits which means that there's a total of 32 bits.
10 . 0 . 0 . 0 / 16
[8]+[8]+[8]+[8] = 32 bits
- The
/16is saying that the first two octets (or 16 bits)10.0.will be your Network Address.
- The next
.0represents your Subnet. - The final octet
.0represents your Device Address.
This diagram shows the relationship between a VPC, a subnet and a device.
What can I do with this knowledge?
This is helpful as you begin assigning new subnets and devices to your VPC. For example, if you want to create two new database servers that are not directly linked to the Internet, you might want to assign them to a subnet
10.0.1.xand provide them with a device id of10.0.1.0and10.0.1.1.
Other Helpful Facts
How many addresses does AWS reserve by default? Each subnet is given 3 addresses.
Subnet Availability Zones
When you create a subnet, you must assign it to an Availability Zone (i.e. us-east-1, us-west-1, etc). It's a one-to-one ratio.
Network Address Translation (NAT)
Underneath the hood, a NAT is a special kind of EC2 instance and here are a few unique characteristics:
- NAT's are specialized EC2 instances so you will be charged accordingly.
- NAT's technically live in a Public Subnet but have access to a private subnet server.
- NAT's allow EC2 instances within our Private Subnet to talk to the outside world.
- NAT's have their own public IP address.
What can I do with this knowledge?
Simple, if you have a private server but you want it to have access to the outside world, you'll need to use a NAT.
DNS Hostnames
When you are creating a VPC, you'll want to say yes to Enable DNS Hostnames. This will allow you to create endpoints that resolve internally and the public internet.
Managing Firewalls

Firewalls allow you, the administrator, to control how your trafffic flows inward and outward. When it comes to managing firewalls within your VPC, you have two tools to work with:
Security Groups
Security Groups help you declare what type of access you want to provide to your servers. In general, you assign Ports to Security Groups so for example, if you want to provide access to a Wordpress website, you may need to allow Port 80 (HTTP), Port 443 (HTTPS), and Port 22 (SSL) to your Security Group.
Access Control Lists
ACL's are similar to Security Groups but with more fine grained control. For example, if you want to block a specific set of IP addresses, you can input that information, into an ACL.
In many ways, the ACL is the second line of defense if your Security Group fails you.
Managing Internet Gateways

The Internet Gateway is a routing table that enables your EC2 instances (within your Public Subnet) to feel like they have their own IP addresses.
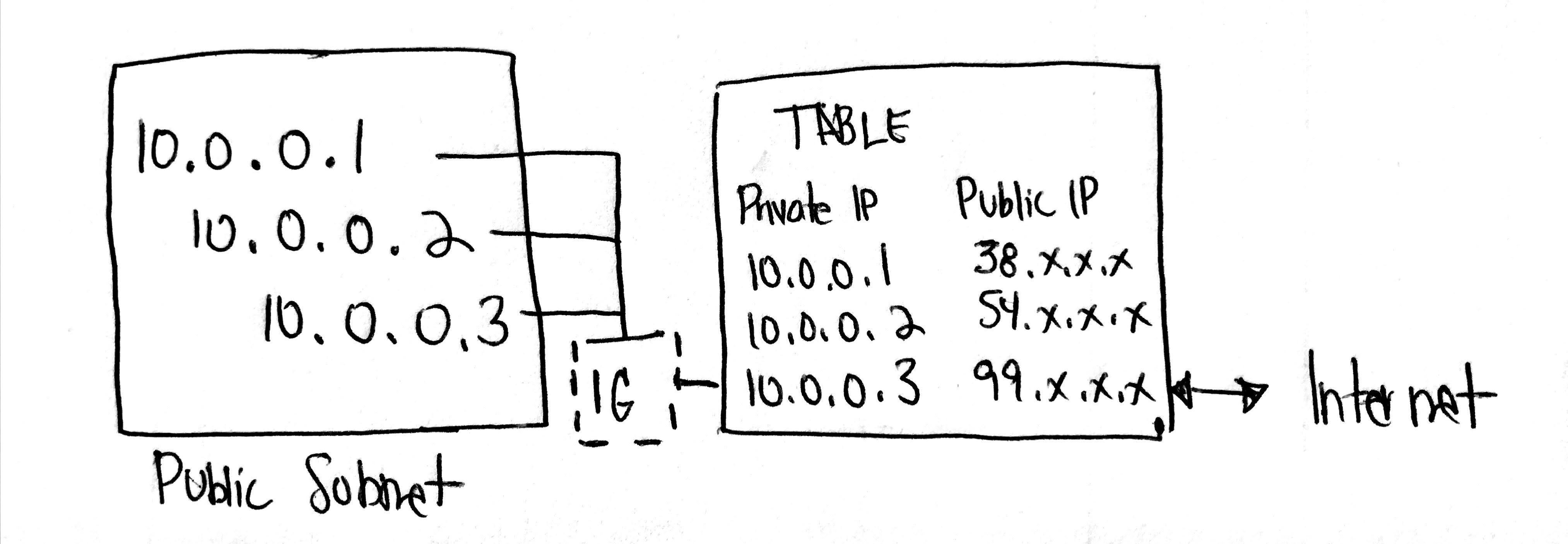
Internet Gateway Facts
- You cannot attach multiple Internet Gateways to a VPC.
Managing Route Tables

This is where you patch things from the outside world to your EC2 instances.
- Create a route table
- Create an out for the route table by assigning
0.0.0.0/0.
The reason why you want to create a new route table that faces the public internet (instead of using your default main) is because if you create a subnet, it will then automatically be assigned to the outside world.
Final Thoughts

There's a lot to learn about VPC's. It's especially hard for web developers, like me, who traditionally work on apps and leave the infrastructure stuff to the DevOps people. That said, times are changing and it's probably important for every developer to become full-stack.
Besides, if you really think about it. If you mess something up, you can just delete it and start all over again. Yes, it's easy and cheap enough for all of us to mess up. So keep trying and over time, it will all start to make sense.